Medical devices and electronic health records have become a way to facilitate better patient care. The substantial development of technology used in an increasing number of hacking and ransomware attacks has made cybersecurity a priority in health care.
Are we ready for the worst?
Hacking incidents might have many varied, harmful effects for healthcare organizations, from leakage of personal data to interruption in the operation of an organisation. When an attack happens, an appropriate strategy of recovery action is crucial [1].
There are many types of cyber threats:
- Black hats – stealing data by, for example, changing the appearance of a website,
- Cryptographic Attacks – revealing encrypted information and transactions or encrypting victims’ data,
- Cybercrime – all crimes committed on computers or the process of deleting traces of crime,
- Denial-of-Service Attacks – stopping or hindering access to services,
- Injection Exploits – entering bad data to interrupt the operation of services,
- Malware – any software changing the normal behavior of a computer in a way that the victim would never allow if they knew about it,
- Privilege Escalation – intentional upgrading of user accounts to get additional privileges,
- Web Security Exploits – searching for weak points in a web browser to get information about users [2],
In research carried out by American scientists, there were 1512 medical data breaches affecting 154,415,257 patient records in America from 2013 to 2017. There were also 128 electronic medical record-related breaches of 4,867,920 patient records, while 363 hacking incidents affected 130,702,378 records. Despite making up less than 25% of all breaches, hacking was responsible for nearly 85% of all affected patient records [3].
Many organisations concentrate on detection and preventive actions in their cybersecurity management. Unfortunately, reactions to incidents are not fast enough. A 2018 study of 2800 respondents from various industries found that 77% do not consistently apply formal incident response plans across their organizations. Half of those organisations admitted that their incident response plans either did not exist or were informal. The number of unprepared organisations could be even higher due to the fact that the medical sector is not as developed as other industries [1].
When an attack happens…
As a result of this research, the Eight Aggregated Response Strategies (EARS) framework was created for cyber incidents.
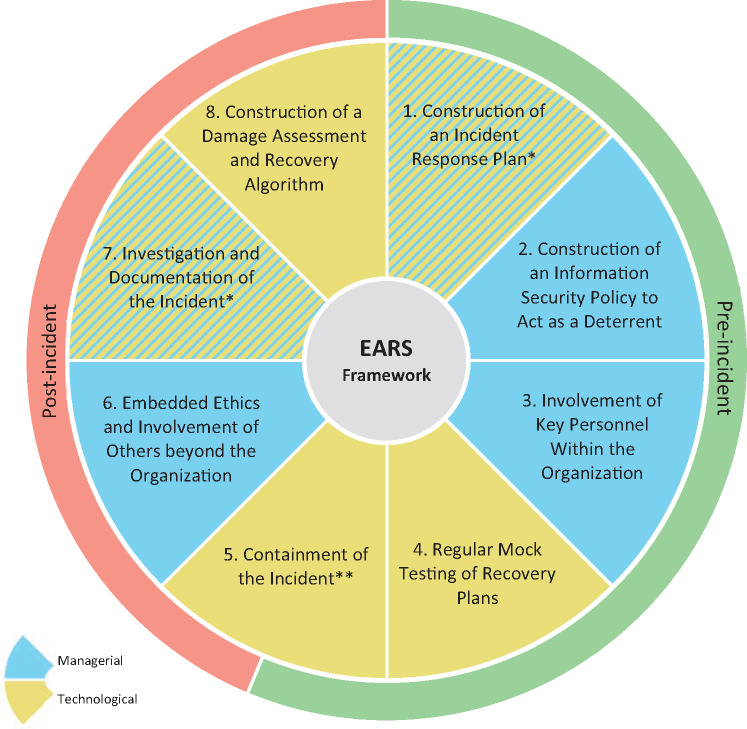
Fig 1. Eight Aggregated Response Strategies (EARS) framework for cyber incidents. *This component is both managerial and technological. **This component is both pre- and post-incidental [1].
Pre-incident actions include:
- Construction of an incident response plan – should be created to guide employees in the event of a cyber incident,
- Construction of an information security policy to act as a deterrent – should be created to deter computer abuse,
- Involvement of key personnel within the organization – key employees should be trained on the importance of information security,
- Regular mock testing of recovery plans – should be introduced to eliminate mistakes,
- Containment of the incident, part A: proactive measures – segmentation of the network [1].
Post-incident actions include:
- Containment of the incident, part B: reactive measures – disconnection from the network in in the event of an incident,
- Embedded ethics and involvement of others beyond the organization – knowledge of the fact that, when an incident happens, it affects stakeholders,
- Investigation and documentation of the incident – investigation should be prompt, thorough and documented, and all evidence should be secured,
- Construction of a damage assessment and recovery algorithm – should be created to delete affected transactions and files [1],
Hurry up! Take care of your data!
Technological development carries great threats. Hackers are constantly inventing more and more new methods to take our personal data. This poses threats to every industry, but especially the medical sector, which is all about people’s health and life. Appropriately implemented response strategies provide the possibility to prevent cyber attacks, to detect them and to deal with their consequences.
Many hospitals have a traditional computer infrastructure, including having their own servers located on the hospital premises. This solution has many risks. Local data storage can lead to irreversible loss of data. Additionally, the operating systems are not updated regularly. Protections that were effective a few years ago are insufficient now. On top of this, all responsibilities for security rest with the hospital.
Trust the clouds
Cardiomatics is a cloud AI tool. It uses AWS to store data and make calculations. Using cloud solutions in an organisation helps to keep data secure. AWS provides tools to control the storage of data and shows who has access to them. It also helps to establish the necessary resources. The cloud infrastructure supplier provides a high stability of service and safeguarding of data. Transferred data is encrypted and can be managed easily. Backups of files are created to ensure that, in the event of unforeseen circumstances, data can be restored. Furthermore, information is replicated to availability zones. If one zone does not work, the other one takes control. Cardiomatics is continuously monitoring website users with specialized tools to identify unauthorized movements. As well as this, there is a hierarchy of accounts which allows access to personal data to be controlled.
Bibliography:
[1] Jalali M.S, Russell B, Razak S, Gordon WJ, “EARS to cyber incidents in health care”, Journal of the American Medical Informatics Association, 01.2019, 26(1):81-90,
[2] Langer S.G, “Cyber-Security Issues in Healthcare Information Technology”, Journal of Digital Imaging, 02.2017, 30(1):117-125,
[3] Ronquillo J.G, Erik Winterholler J, Cwikla K, Szymanski R, Levy C, “Health IT, hacking, and cybersecurity: national trends in data breaches of protected health information”, 06.2018, 1(1):15-19.


